I'm back
I’m back and ready to start working. Vacation is over :) Yesterday I got a private order from my old customer. The SnapChat crypto. It should be interesting…
Will be offline next 10 days
Subj.
BTW, here is a pre-pre-pre-alpha of my own console with chess and postgraduate student girls:
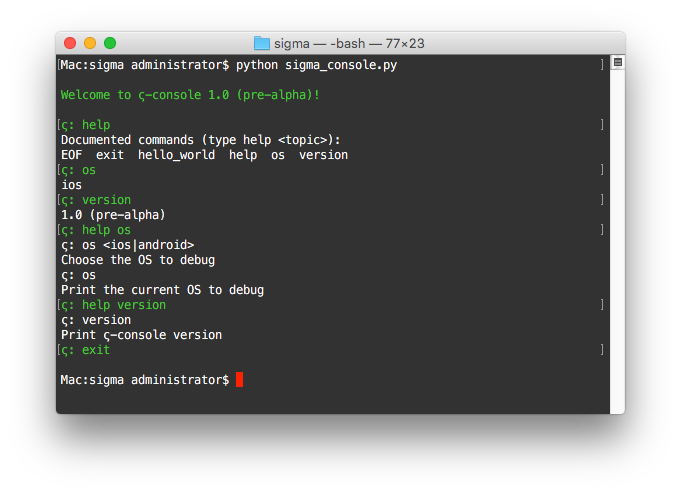
I'm going to build my own LLDB console!
I wrote LLDB console sux, and that’s true! Look at mem read. I can use expression for an address, but can’t use if for a count of bytes to read:
(lldb) mem read <can use expression> --count <can't use expressions>
Thouns of such weird things are in LLDB console. “I’m going to build my own theme park! With blackjack! And hookers!” (c)
LLDB console sux
A simple test.py with a custom LLDB command test:
import lldb
def test(debugger, command, result, internal_dict):
target = debugger.GetSelectedTarget()
target.GetProcess().Continue()
def __lldb_init_module(debugger, internal_dict):
debugger.HandleCommand('command script add -f test.test test')
A quick word about XLLDB
I’ve started XLLDB project about a week ago. It’s a reverse engineering mini-framework written in pure Python. It’s OOP-friendly and suitable for automating reverse engineering tasks. Actually, I could continue using “raw” LLDB Python APIs, they are more or less stable and pretty useful. However, some things made my Python code more crap that usual.
Page 1 of 2 Next »